With our Checkpoint Insight Tool you go beyond generic
benchmarks. Start creating your security baseline situation.
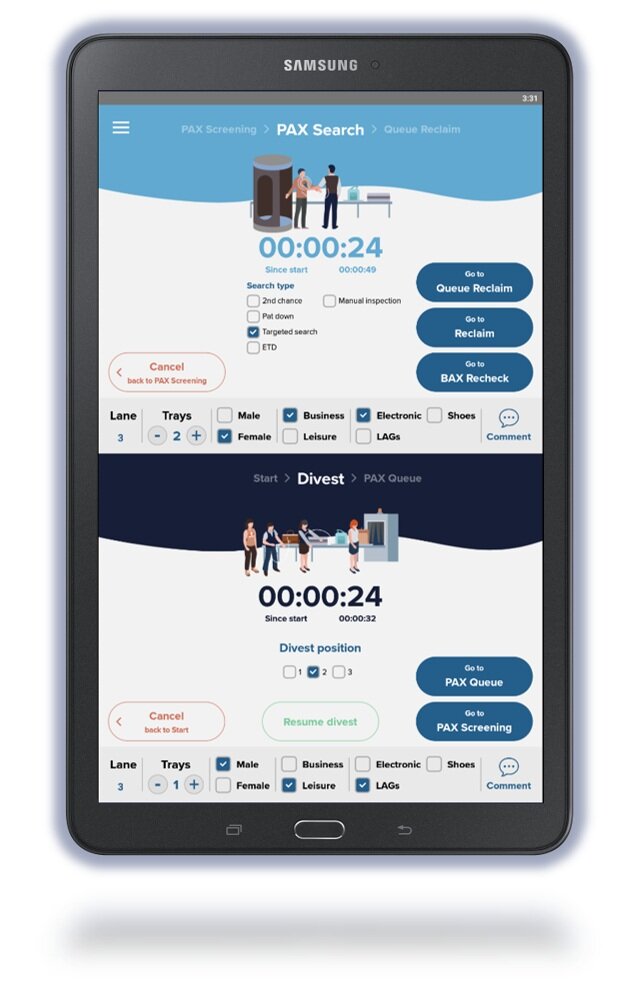
Our security checkpoint capture
method is now available as a
ready to use tablet application.
Presenting process insights in an interactive web-based (BI) reporting environment. Ready to adapt to your
requirements for process improvement.
A Value adding instrument for a wide selection of security checkpoint stakeholders
Airports
Continuous monitoring
Process optimisation
Procurement of equipment
Increase stakeholder collaboration
Security Operators
Accurate KPI monitoring
Increase planning efficiency
Steer day-to-day operations
Refinement of training program
Equipment suppliers
Pre-solution assessment
Post-solution assessment
Trialling of novel functionality and algorithm upgrades
A 3-in-1 measurement platform
Including three seperate measurement tools. The main tool focuses on measuring the security process from start to end, the other two for measuring occupancy and simultaneity levels at divest and reclaim.
Security Process measurements
Facilitating accurate passenger action registration.
Intuitive and consistent guidance through process and procedures.
Register passenger profiles and content types.
Register active and passive passenger processing.
Comment function to capture anomalies.
Facilitation for all common checkpoint configurations.
simultaneity measurements
Main approach for capturing Divest and Reclaim-specific passenger processing.
Equal measurement approach for both Divest and Reclaim processes.
Output of simultaneity capture is used to determine accurate process capacities at certain operational hours.
Occupancy measurements
Capture divest spot assignment process in parallel security lanes.
To be used for calculating availability and divest occupancy levels in various operational instances.
Output data provides for occupancy level per position.
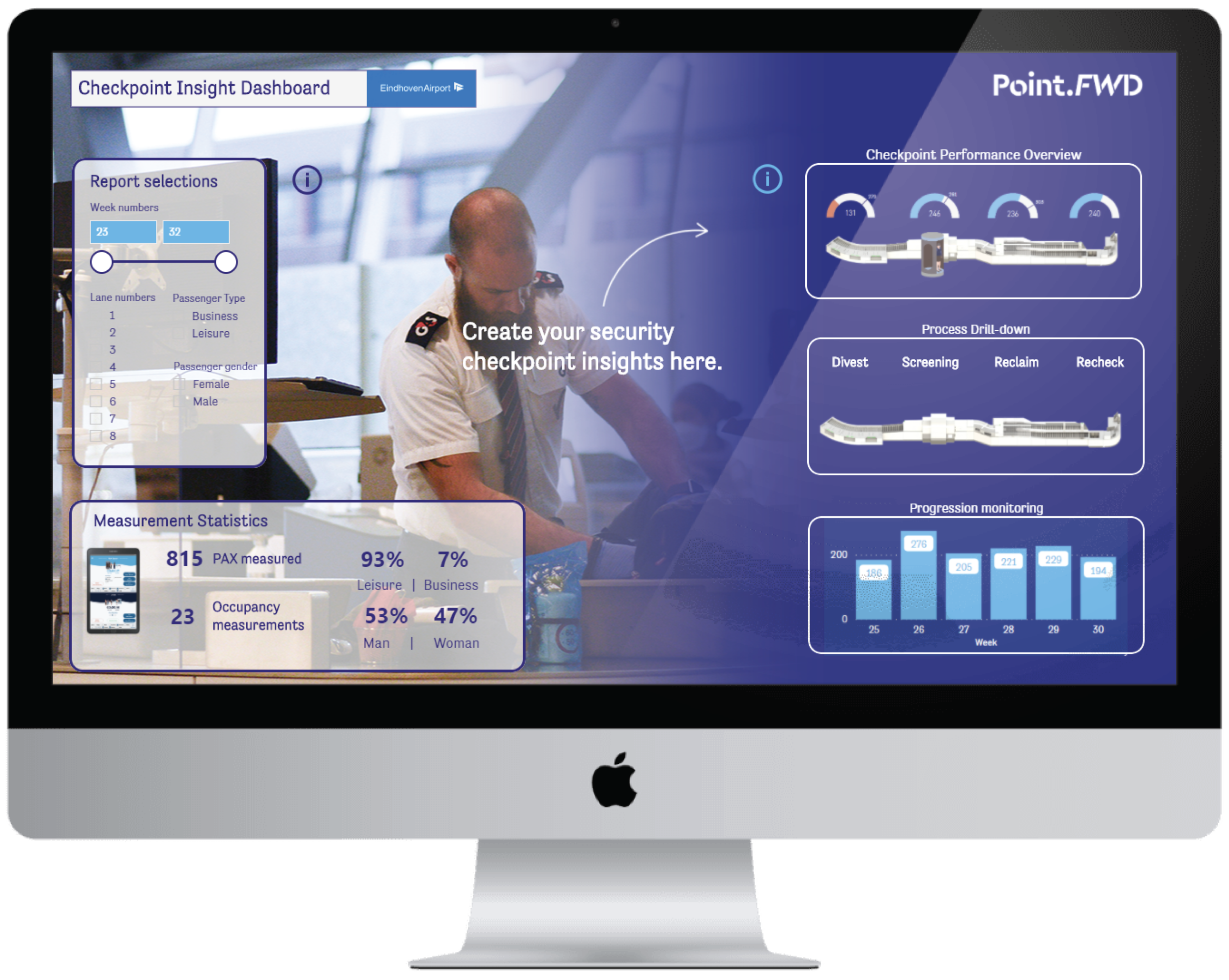
Numerous output possibilities with Interactive (BI) Reporting tools
Collected data is detailed and checkpoint specific, and is therefore of significant value for a versatility of purposes and application areas. Below included is an example of such an output presentation; a Security Monitoring Dashboard, including multiple levels of insight and control.
Level 1: Extensive process insights on security lane level for discovery of bottlenecks and enhancement potential.
This dashboard is intended as the first go-to when getting your most recent checkpoint performance insights on screen.
It should really enable the end-user to deep-dive into their process of interest for a specific timeframe or security lane selection.
Level 2: Isolated process drill down for in-depth process analyses and initiation of enhancements.
At this level, every KPI or measure can be fetched for the specific passenger / process characteristic to study. In this depicted example, rechecked luggage can be analysed for the time needed to resolve alarms.
This step could be particularly helpful when initiating specific process or CONOP changes.
Level 3: Progression monitoring for KPI specific comparisons over time.
This dashboard acts as the basis for putting focus on enhancement, being able to really closely get grip on one single KPI (i.e. Tray per Passenger, Preparation time)
With this specific board, your trends, either negative or positive will become noticeable and actionable.
Creating solid starting points for successful security checkpoint change.
With specific utilisation aims for:
COVID-19 operations recovery monitoring;
Independent baseline performance measurements;
Security equipment trial progression monitoring;
Checkpoint optimisation as guiding instrument.
Latest news and updates around CIT
Success exists when making things measurable.
Avoid hesitation and take control.
This is just a glimpse of what CIT is. Our team is always available showing you around, to provide more information and to address your security checkpoint challenge.
Go to our Modelling and Simulation Tools