A holistic view is key when upgrading or re-designing the security checkpoint with any technology or security measure. It is certainly not a matter of replacing a machine or adding an algorithm. Moreover, it is about rebalancing all processes to accommodate for the technology implementation(s) as initiated, and obviously this is no different for APIDS implementation. The expectation (and promise) of APIDS is that less screeners per lane are required to screen the same number of images, but with the requirement that centralized image analysis – or networked screening – is in place to be able to gain the potential.
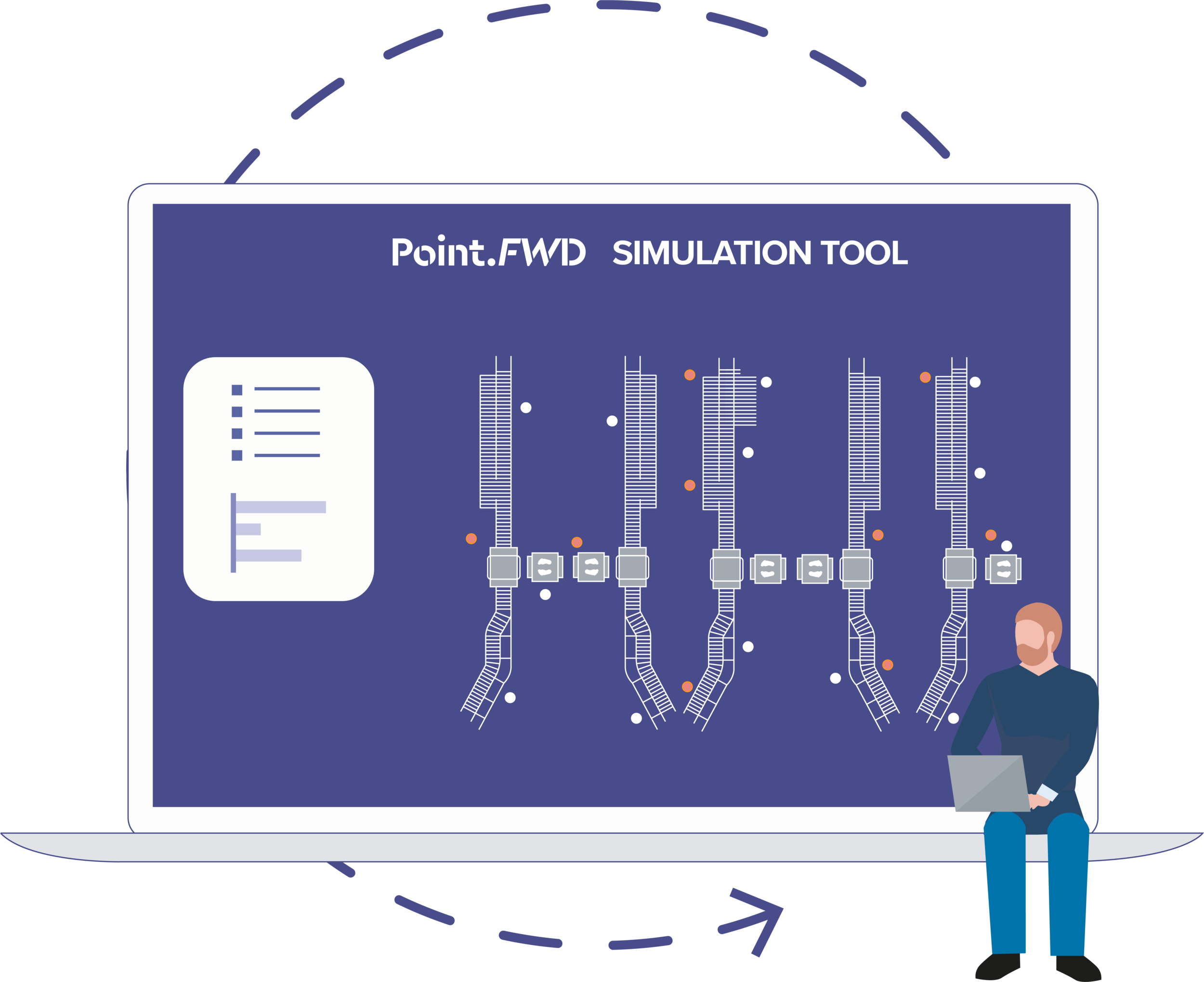
The optimal security lane and checkpoint design is unique for every airport and can even vary across the airport for the different checkpoints. For this reason, using process characteristics from the local situation is essential when developing for a future lane concept. Together with assumptions for future operation of APIDS systems and CONOPs, functional lane designs can be modelled and simulated to assess the impact on output figures such as passenger and tray throughput, (decreased) staffing of personnel and expected workloads. Doing so, various functional design scenarios can act as input for operational business case assessments, resulting in confidence and accuracy in strategic decision-making.
3. Validate APIDS setups and start optimization
Trialing a new combination of systems and CONOPs in a real airport environment will always be the best step towards solution validation. That is, we can model and calculate the best we can, however, the true value (and pitfalls) of APIDS systems should be concluded in a real-life operational environment with all uncertainties present. It should always be the step in between initial design and final roll-out of a solution. Furthermore, in the trial setup, end-users are confronted with APIDS and will get trained or become known how to adapt to the new way of working. The insights that were gained during an APIDS trial should of course serve as input for simulations of final checkpoint design, lane concept development or even tender specification.
One of the main focus points to trial APIDS solutions in the AvSec checkpoints is to closely monitor every part of the coherent security process. Data capture and analysis helps to critically assess whether, where in the process and to what extend changes have occurred. Monitoring of APIDS technology trials can best be done using omni-source data collection – including machine, manual or sensor data. The reason for doing this is to be able to tackle any differentiation in process performance that might be present, including bottleneck shifting, decreased alarm resolution times or increased IPP due to seasonal change.
4. Start implementation and continuous monitoring of APIDS solutions.
The start of deployment of APIDS systems should be seen as the start of various other projects. Fully dependent on the CONOPs in which APIDS will be implemented, it is expected that new waves of technology will get certified and that other process CONOPs become available to the early airports adopting the primary APIDS technology. Therefore, continuous monitoring the operation remains key to be able to optimize for the most beneficial process including staffing and work instructions.